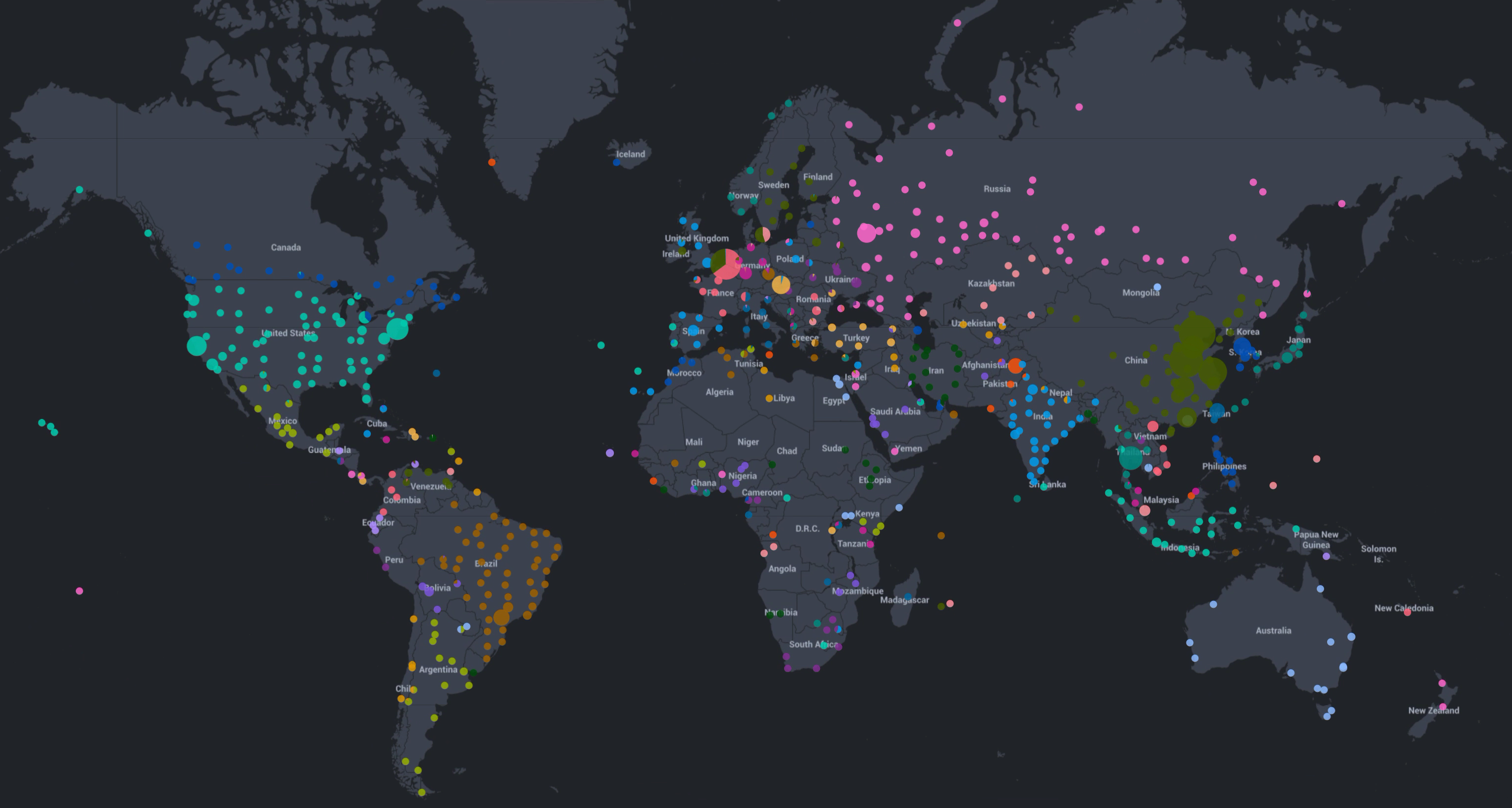
Below0Day deployed HoneyDB honeypot agents across 18 countries to monitor and analyze attack patterns. We configured these agents with services like RDP, VNC, SSH, FTP, MySQL, WebLogic, Elasticsearch, Telnet, and Redis.
Project Setup
We distributed honeypot agents strategically worldwide, with some regions hosting multiple agents. Data collected from these agents is visualized through Splunk dashboards for analysis and reporting.
Monitored Services
- RDP
- VNC
- SSH
- FTP
- MySQL
- WebLogic
- Elasticsearch
- Telnet
- Redis
Top Attack Origins
Our research identified the most active attacking IP addresses:
| IP Address | Location | Organization |
|---|---|---|
| 202.139.198.181 | Thailand | Government Data Center |
| 111.22.113.168 | China | China Mobile - Changsha |
| 45.81.39.103 | Netherlands | Delis LLC - Amsterdam |
| 218.92.0.107 | China | Chinanet - Jinan |
| 61.177.172.13 | China | Chinanet - Jiangsu |
| 185.220.101.35 | Germany | Tor Exit Node |
| 218.92.0.56 | China | Chinanet - Jinan |
| 89.248.165.55 | Netherlands | Censys Scanner |
The top attacking IPs showed concentrations from cloud providers, ISPs, and datacenter operators across various ASNs.
Attack Targets
The honeypots tracked which agents received the most attention, revealing geographic hotspots for malicious activity.
Services Under Fire
Analysis showed RDP, SSH, and MySQL were among the most frequently targeted services across the honeypot network.
Data Sharing
We committed to sharing findings via our Twitter account (@below0day) and GitHub repository, making the honeypot data publicly available for security researchers.