WannaCry Ransomware Utilizing NSA Exploits
Update 5/12/17 19:30 CST: An “accidental hero” (credited to @MalwareTechBlog) discovered a kill switch to halt the ransomware’s spread. “Even though the domain has been sinkholed stopping the spread of infections, new variants of wormable ransomware campaigns are only to be expected in the near future.”
Update 5/13/17 10:30 CST: Microsoft released emergency patches for previously unsupported systems (XP/8/2003), available via their security advisory.
What is WannaCry?
Early Friday, May 12th, ransomware variants (Wcry/WanaCrypt0r/WannaCry/WanaCypt0r/Wanacryptor) began spreading rapidly across Europe. Kaspersky Lab’s Chief Security Expert described it as a “worldwide ransomware outbreak.”
Technical Details:
- Exploits EternalBlue, released by ShadowBrokers
- Remote code execution vulnerability targeting SMB v1 protocol
- Patched via MS17-010 (released March 14th)
- Checks for DOUBLEPULSAR before loading payload
- Spread to 74+ countries within hours
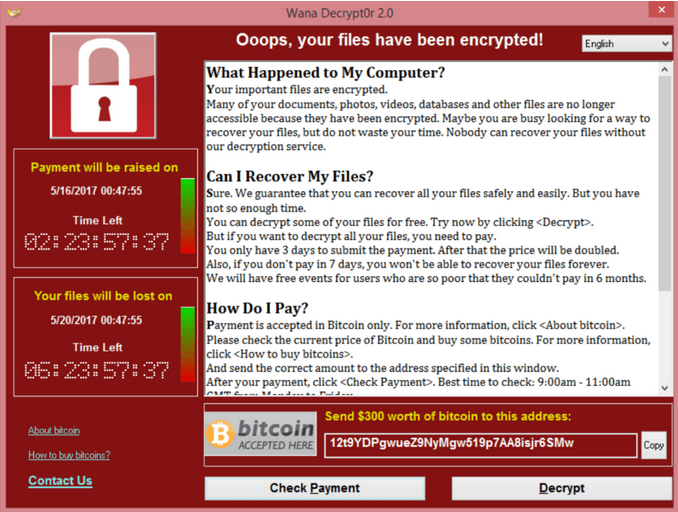
- Ransom demands: $300-$600 in Bitcoin
Bitcoin Addresses
- https://blockchain.info/address/13AM4VW2dhxYgXeQepoHkHSQuy6NgaEb94
- https://blockchain.info/address/115p7UMMngoj1pMvkpHijcRdfJNXj6LrLn
- https://blockchain.info/address/12t9YDPgwueZ9NyMgw519p7AA8isjr6SMw
Confirmed Tor C&C Addresses
- gx7ekbenv2riucmf.onion
- 57g7spgrzlojinas.onion
- xxlvbrloxvriy2c5.onion
- 76jdd2ir2embyv47.onion
- cwwnhwhlz52maqm7.onion
Targeted File Extensions
The ransomware targets 149+ file types including:
Documents: .doc, .docx, .xls, .xlsx, .ppt, .pptx, .pst, .ost, .msg, .eml, .vsd, .vsdx, .txt, .csv, .rtf
Media: .jpeg, .jpg, .bmp, .png, .gif, .raw, .tif, .tiff, .nef, .psd, .ai, .svg, .djvu, .wav, .mp3, .flv, .mkv, .mp4, .avi, .wmv, .mov
Archives: .zip, .rar, .7z, .tar, .tgz, .gz, .bz2, .iso, .backup
Source Code: .php, .jsp, .asp, .java, .rb, .py, .js, .cpp, .c, .cs, .vb, .bat, .cmd, .ps1, .sh
Databases: .sql, .mdb, .db, .sqlite3, .accdb
Prevention Recommendations
- Apply MS17-010 patches immediately
- Ensure complete backups of critical systems
- Block inbound traffic on ports 445/137-139 and 3389
- Disable SMB v1 protocol
- Implement network segmentation
- Disable Microsoft Office Macros
Kill-Switch Domains (DO NOT BLOCK)
- iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com
- ifferfsodp9ifjaposdfjhgosurijfaewrwergwea.com
- iuqssfsodp9ifjaposdfjhgosurijfaewrwergwea.com
- ayylmaotjhsstasdfasdfasdfasdfasdfasdfasdf.com
- lazarusse.suiche.sdfjhgosurijfaqwqwqrgwea.com