Update 6/28/17 19:21 CST: Following deeper examination of Petya/ExPetr/NotPetya’s encryption methods, Kaspersky determined that “malware campaign was not designed as a ransomware attack for financial gain. Instead, it appears it was designed as a wiper pretending to be ransomware.”
Petya
On June 27th morning, a ransomware variant named Petya dispersed rapidly worldwide, with confirmed infections in Russia, Ukraine, India, and Europe. The Chernobyl nuclear power plant was compromised and switched to manual emergency protocols. Though U.S. infection rates remained low initially, widespread infection was anticipated.
Petya originated from Janus Cybercrime Solutions in 2015 as a Ransomware-as-a-Service offering via Tor. Kaspersky Labs identified this variant as previously unseen, naming it NotPetya. This iteration leveraged the NSA’s EternalBlue exploit, which targets SMBv1 (CVE-2017-0144 - patched March 14th) and WMI for network lateral movement - identical distribution method to WannaCry from the prior month.
Distinguishing itself, Petya lacked WannaCry’s kill-switch domain. The initial infection vector appeared to originate from a software update distributed by Ukrainian financial company MeDoc.
Technical Details
Unlike conventional file-encrypting ransomware, Petya encrypts the Master File Table (MFT), restricting computer access. Upon completing encryption rapidly, Petya triggers a blue screen (BSOD) forcing system restart.
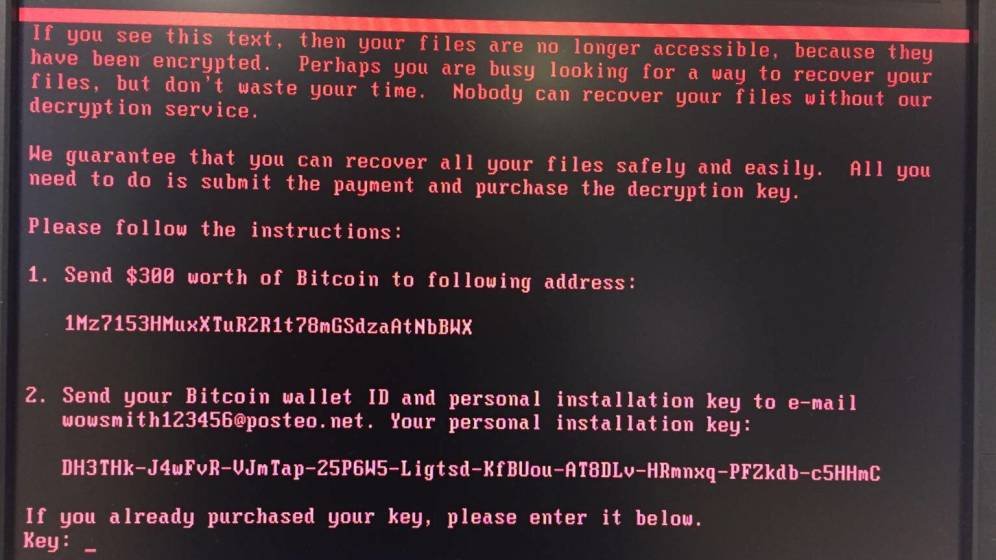
Ransom Message:
“If you see this text, then your files are no longer accessible, because they are encrypted. Perhaps you are busy looking for a way to recover your files, but don’t waste your time. Nobody can recover your files without our decryption service.”
Attackers demanded $300 via Bitcoin for decryption. However, German email provider Posteo blacklisted the contact address, effectively preventing ransom communication. DO NOT PAY.
Critical Guidance
According to @HackerFantastic, machines become encrypted post-reboot. If infected:
- DO NOT restart the machine
- Power off immediately
- If reboot occurs and CHKDSK displays, power down and use alternative machines or LiveCD for file recovery
Bitcoin Addresses
https://blockchain.info/address/1Mz7153HMuxXTuR2R1t78mGSdzaAtNbBWX
Targeted File Extensions
.3ds, .7z, .accdb, .ai, .asp, .aspx, .avhd, .back, .bak, .c, .cfg, .conf, .cpp, .cs, .ctl, .dbf, .disk, .djvu, .doc, .docx, .dwg, .eml, .fdb, .gz, .h, .hdd, .kdbx, .mail, .mdb, .msg, .nrg, .ora, .ost, .ova, .ovf, .pdf, .php, .pmf, .ppt, .pptx, .pst, .pvi, .py, .pyc, .rar, .rtf, .sln, .sql, .tar, .vbox, .vbs, .vcb, .vdi, .vfd, .vmc, .vmdk, .vmsd, .vmx, .vsdx, .vsv, .work, .xls, .xlsx, .xvd, .zip
Sample Hashes
027cc450ef5f8c5f653329641ec1fed91f694e0d229928963b30f6b0d7d3a745
8143d7d370015ccebcdaafce3f399156ffdf045ac8bedcc67bdffb1507be0b58
Indicators of Compromise (IoC) IPs
- 84.200.16.242
- 95.141.115.108
- 111.90.139.247
Prevention Recommendations
- Apply MS17-010 patches
- Disable SMBv1
- Disable WMIC
- Ensure critical systems maintain complete backups
- Implement network segmentation
- Restrict user privilege levels
For questions or support, please contact us.